Quick Summary:
Boost your salesforce security with the key best practices, including multi-factor authentication, robust password policies, and data encryption. From IP restriction to continuous monitoring, this blog highlights crucial measures. These salesforce security best practices provide an extra layer of defenses against evolving threats, ensuring data integrity and user trust.
📝 In this blog, we’re going to discuss…
Salesforce has become a critical SaaS platform for organizations to manage customer relationships, sales, marketing activities, and other business operations. However, the sensitive data stored and transmitted through Salesforce also makes it an attractive target for cyber criminals. According to the Salesforce report, managing data security has various pain points.
- 35% have faced issues in Third-party security management
- 20% have faced issues in Mobile device security management
- 14% have faced issues in Keeping up with the compliance regulations
- 13% have faced issues with resource constraints
- 10% have faced issues in Vulnerability management
- 4% have faced issues in User behavior
- 2% have faced issues in Managing proactive hacking prevention measure
- 1% have faced issues in Auditing
These stats prove that it is paramount to employ salesforce security best practices.
A security incident involving Salesforce could expose sensitive customer data, intellectual property, financial data and other proprietary business information. The consequences of such a breach include reputational damage, legal liability, and financial losses. That’s why having a robust security strategy for Salesforce is a fundamental business requirement. Companies need to take dynamic steps to safeguard their Salesforce ecosystem against internal and external threats. A layered approach to security combines people, processes and technology to protect Salesforce across multiple levels.
Both system configurations, user policies & behaviors play key roles. Ongoing security activities such as assessments, monitoring, patching and training are critical as well. The security landscape evolves rapidly, and threats to Salesforce can emerge at any time. With proper governance and the right best practices, companies can effectively secure Salesforce, manage risks, maintain compliance and minimize their attack surface. A comprehensive security program is crucial not just for technology defense but also for upholding trust with customers.
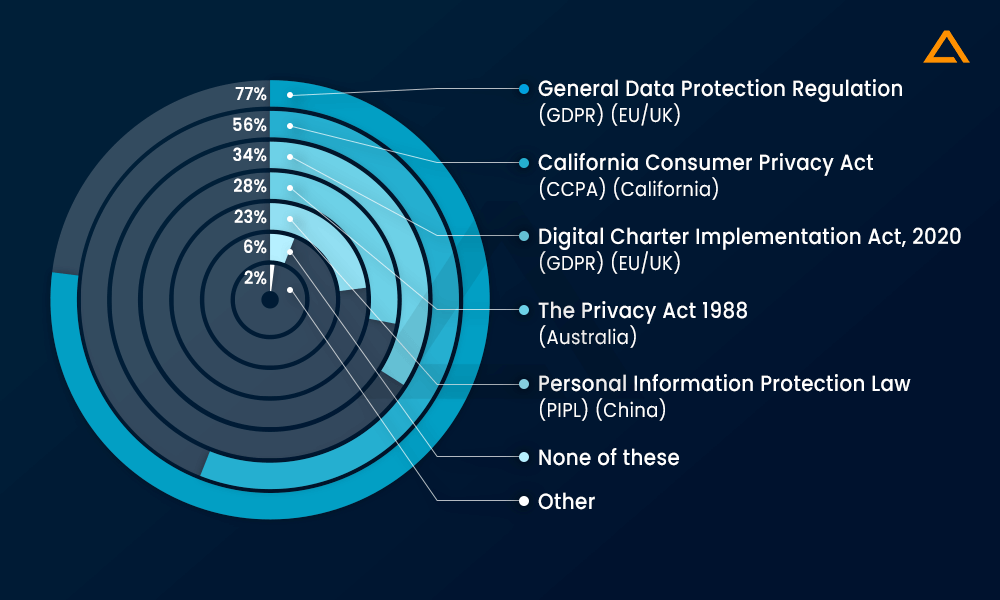
While recognizing the difficulties associated with compliance management, many global IT leaders state that they have reached high standards of international data compliance. Nonetheless, the vision of further technology investments emerges as a potential solution to simplify the complexities characteristic in staying well-informed of international regulations.
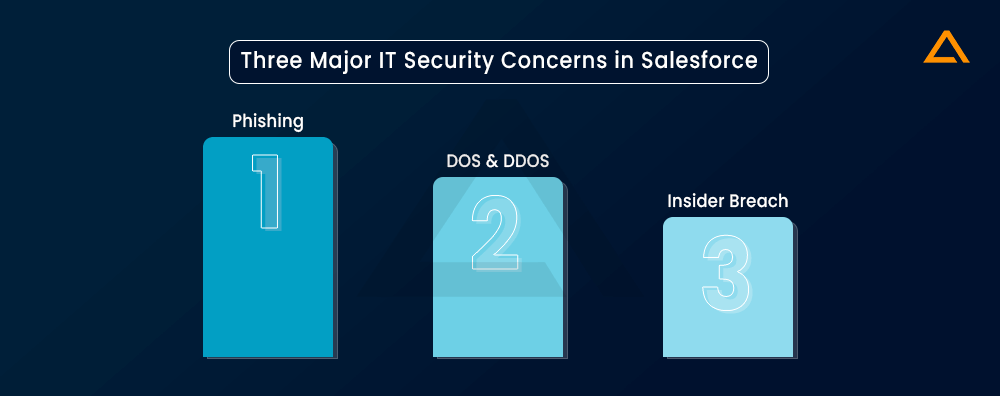
What are the Three Major IT Security Concerns in Salesforce?
According to the recent Ponemon Institute survey, 52% of organizations reported an increase in cyberattacks. With the persistent threat landscape. IT leaders in our survey identified phishing, DOS/DDOS attacks and insider breach or misconfiguration as their top security concern.
Now let’s understand a bit about these challenges:
Phishing
Phishing involves dishonest strategies, which is often done through emails or messages, to trick individuals into sharing sensitive information. In this, the attacker mimics a trustworthy entity, abusing human weakness to gain unauthorized access or compromise personal data.
Mitigation
To fight against the phishing attacks, you need to keep a few things in mind. They are as follows:
- Awareness Training
- Email Filtering
- Multi-factor authentication
- Incident response plan
- Report Mechanism

DOS & DDOS
In basic terms DOS (Denial of Service) & DDoS (Distributed denial of service) attacks overwhelm a website making it inaccessible to users. DOS comes from a single source, while DDoS involves multiple sources, intensifying the impact for disruption
Mitigation
To secure your project from DOS and DDOS attacks following are the things that you need to keep in mind:
- Network Monitoring
- Scalable Infrastructure
- Firewalls and IPS
- Content Delivery Networks (CDNs)
- Rate Limiting
- Incident Response Plan

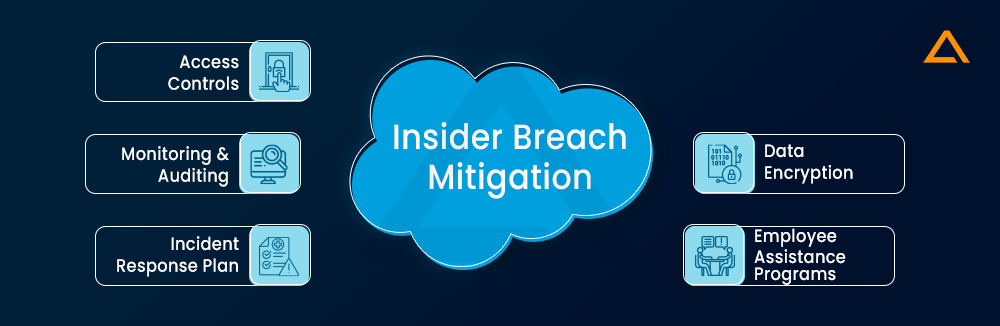
Insider Breach
An insider breach occurs when a person with authorized access to an organization’s systems or data intentionally or unintentionally exploits that access to compromise sensitive information, posing a significant threat to data security and confidentiality.
Mitigation
This is one the worst things that any company can face, following are some of the things that you should keep in mind.
- Access Controls
- Monitoring and Auditing
- Incident Response Plan
- Data Encryption
- Employee Assistance Programs
Data protection plays an important role in organizations, when not taken seriously it can lead to deadly consequences. To enhance security & guarantee the integrity of your organization’s information. Salesforce offers a series of functionalities, measures & tools that we have condensed into a list of salesforce security best practices.

Searching for IT Superstars?
We’re the AugMENTIONED Ones! 👀🌟”
Aglowid provides the best IT Staff Augmentation Solutions
Salesforce Security Best Practices
While Salesforce is committed to provide security and provides tools and resources you need to protect your data. However, it is important to remote that its still your responsibility to apply security controls and implement best practices. Here are some great ways you can incorporate data security into your organization.
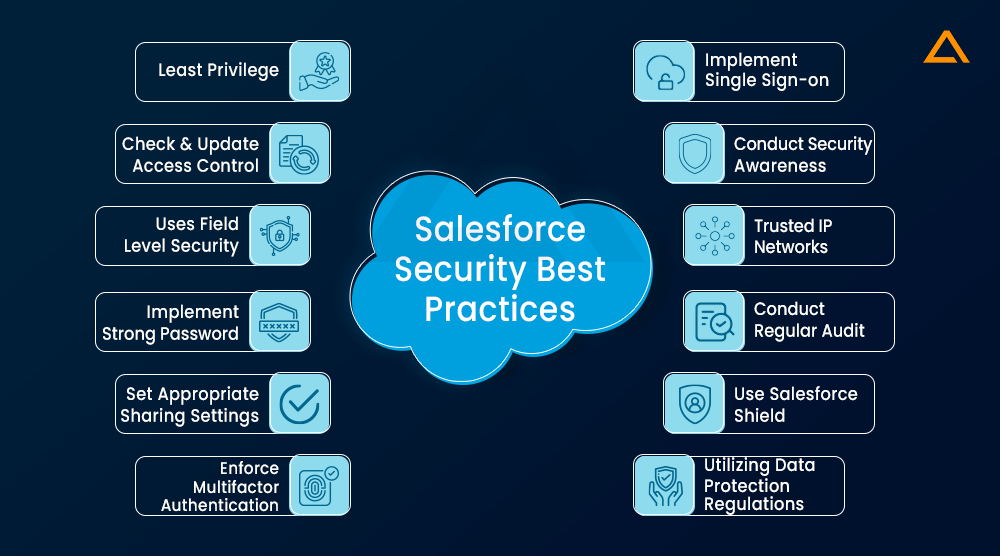
Least Privilege
The principle of minimized privilege suggests that users should be allowed the minimum permissions necessary to perform their duties. This motion reduces the risk of unauthorized data access or modification. Avoid giving broad permissions such as View All, Modify All, or Delete unless it’s absolutely necessary.
Periodically Check & Update Access Control
As the organization undergoes changes, the corresponding adjustments in data access needs are inevitable. Ensure the ongoing relevance of profiles, permission sets, and field-level security settings by conducting regular reviews and updates to align them with the current requirements.
Use Field Level Security for Sensitive Data
Ensuring the security of sensitive data is important, and field-level security plays a crucial role. Whenever a new field is introduced or a profile undergoes updates, it is important to conduct a thorough review of field-level security.
Implement Strong Password
To enhance the password security, enforce complexity standards, requiring passwords to be 12–15 characters long with a mix of alpha-numeric characters, special symbols, and a combination of uppercase and lowercase letters. Additionally, establish a regular password rotation policy, with options for expiration every 60, 90, or 180 days, minimizing the risk of unauthorized access through compromised credentials.
While a 30-day rotation is a robust practice, it may be met with some resistance from users. Furthermore, prohibit the reuse of old passwords and specific phrases, like the company name, to frustrate attackers attempting to exploit credentials across various services. Implementing this salesforce security best practice can effectively reduce the vulnerabilities that can be used to exploit the brute force and credential stuffing attacks that question the integrity of company.
Set Appropriate Sharing Settings
Salesforce provides administrators with the flexibility to customize login requirements and limits, tailoring security measures based on diverse user profiles. This includes two key considerations:
At the Organization-Wide Default (OWD) level, administrators can define the default level of access users possess. By strategically restricting access to sensitive data, this setting acts as a preventive measure against unauthorized users attempting to view critical information.
For more nuanced control, administrators can employ Profile-Level Settings to configure login hours and IP restrictions. This level of granularity ensures that users can only log in during specific hours and from trusted IP networks, effectively minimizing the risk of unauthorized access.
Enforce Multifactor Authentication
There are three ways in which you can apply the multifactor authentication. First one is global multifactor authentication, second is using Multifactor permission sets, and lastly there is Salesforce authenticator app. Let’s take a look at each one them in detail.

Global Multifactor Authentication
You can start by rolling out Multi-factor Authentication (MFA) for all the users. Salesforce orders compulsory universal usage, irrespective to the privilege level roles. This complete approach ensures that every available account is protected, which eliminates any vulnerabilities in the system for attack to exploit. To setup navigate to setup > Identity Verification > MFA. Here you’ll need to check all the options required by MFA for all users, enable alternative verification methods, and mandate identity verification during MFA registration.
Using MFA Permission Set
For a phased implementation, create MFA permission sets and assign them to specific user groups in batches. This gradual approach allows the incremental adoption of MFA without disrupting daily business operations. To set this up, Create a MFA Permission Set > Add MFA User Login Permissions > Assign Users.
Using Salesforce Authenticator App
Additionally, promote the use of the Salesforce Authenticator app, offering users a convenient and secure method for MFA through push notifications or time-based one-time passwords (TOTPs). Embracing these practices ensures a robust MFA implementation without overwhelming user support lines.
Implement Single Sign-on
Simplifying the user access by getting Salesforce integration services across Salesforce and integrated applications, single sign-on allows users to just login once and it will grant access to all the platforms. SSO centralizes the authentication, provides user convivence, easing administrator access management. For effective SSO implementation it relies on the key best practices.
Start by integrating with a trusted Identity Provider (IdP) to establish a secure connection between your organization’s user directory and Salesforce. This integration streamlines user provisioning and deprovisioning procedures.
Leverage Lightning Login, a feature ensuring secure access with a single click. Lightning Login employs device recognition and multi-factor authentication (MFA) for a seamless yet secure login experience.
Remember, SSO requires a third-party connection, and you can refer to a dedicated module for guidance on setting it up.
As a Salesforce administrator, prioritizing data security is crucial. The platform’s multitenancy and metadata-driven nature underscore the need for robust security measures. Mastery of user authentication, along with best practices for multifactor authentication, single sign-on, password management, and login requirements, establishes a fortified security framework.
Vigilant monitoring of the Salesforce system stays ahead of potential threats, instilling user confidence, protecting valuable data, and fostering a secure Salesforce experience. Together, these practices create a resilient Salesforce fortress, ensuring data integrity and confidentiality for sustained success in the digital age.
Conduct Security Awareness
As you find the top Salesforce implementation partner to Implement a security awareness program to educate stakeholders on potential risks and best practices. Regularly conduct informative sessions emphasizing the significance of vigilance and strict adherence to recognized security protocol. This proactive approach ensures a well-informed user base, reducing vulnerabilities and contributing to the establishment of a robust and secure organizational environment. Keeping users abreast of evolving threats fosters a culture of collective responsibility, enhancing overall cybersecurity resilience.
Trusted IP Networks
Leverage the ‘Trusted IP’ networks feature to enhance salesforce security. By configuring trusted IP ranges, administrators can specifically allow authorized locations for user access. This ensures that the salesforce is accessed only from designated, secure networks, mitigating the risks of unauthorized logins. Implementing this feature adds an additional layer of protection, aligning with best practices to safeguard sensitive data and fortify the overall security posture of your Salesforce environment
Conduct Regular Audit
Regularly auditing your salesforce environment is crucial for identifying & addressing potential security issues proactively. Salesforce offers a range of tools, including the setup audit trail, login history, and field history tracking, to facilitate these audits. By conducting regular reviews through these tools, administrators can detect and rectify security concerns before they escalate into significant problems contributing to a secure Salesforce infrastructure.
Use Salesforce Shield
For organizations who requires complex security, Salesforce offers an additional layer of security and governance tools called Salesforce Shield. This salesforce tool includes Event monitoring, platform encryption, and field audit trail.

Platform Encryption
Stores the data in rest, ensuring that the data remains secure when stored in Salesforce.
Event Monitoring
It will provide the visibility into the usage & behavior of your salesforce app helping you in identifying potential policy violations or any harmful activities.
Field Audit Trail
It lets you define the policies to retrieve the archival history stored in the database up to 10 years. This ensures the industry regulations and compliance.
Utilizing Data Protection Regulations
Stick to data protection regulations like GDPR and CCPA enforces added responsibilities on companies for safeguarding customer data. Salesforce prepares organizations with tools and features to enable compliance with these regulations, emphasizing a shared responsibility for adherence. Users play an important role in upholding compliance by consistently conducting audits. These regular audits, utilizing Salesforce tools like the setup audit trail, login history, and field history tracking, serve to identify and rectify potential security issues before they escalate into more significant problems.

Consent Management
Ensure explicit customer consent is obtained before collecting and processing their data, utilizing Salesforce’s features for efficient consent management.
Data Minimization
Embrace data minimization by collecting only essential information, adhering to the core principles of both GDPR and CCPA.
Right to Access and Erase
Uphold individuals’ rights to access and erase, facilitated by Salesforce’s tools designed to streamline such requests in compliance with GDPR and CCPA.
Data Protection by Design & Default
Implement Data Protection by Design and Default, integrating protective measures seamlessly into processing activities and business practices with Salesforce’s adaptable security settings.
Wrapping up!
Let’s sum up by saying that Salesforce security necessitates a planned and proactive approach. By implementing the recommended best practices, businesses may strengthen their Salesforce environment and ensure data security, privacy, and compliance with legal requirements. Establishing a strong security framework begins with prioritizing user training, single sign-on, multi-factor authentication, and regular audits. Salesforce administrators can establish an all-encompassing security posture by incorporating consent management, data minimization, and data protection by design. This unwavering commitment to security protects confidential data and builds user trust, fostering a robust and dependable Salesforce encounter.



 Say
Say